Managed Detection and Response (MDR) Services from Six Degrees
Organisations need advanced cyber protection combining automation, human expertise and 24x7 capabilities to defend against the contemporary threat landscape. Our service provides these capabilities, all delivered from a UK-onshore CSOC with UK Security-Cleared analysts.
Download the Data SheetSections
What is MDR (Managed Detection and Response)?
MDR is multi-layered protection that can detect and respond automatically to a threat before it becomes a breach.
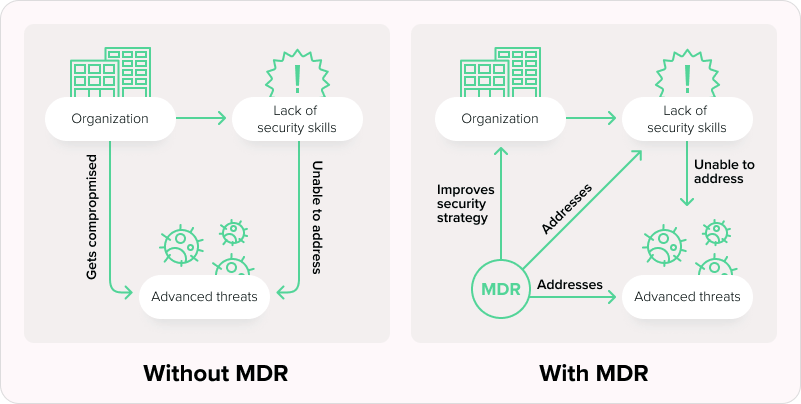
MDR is multi-layered protection that can detect and respond automatically to a threat before it becomes a breach.
How Six Degrees MDR solves cyber security challenges
MDR provides the people, processes and technology needed to match the evolving threat landscape. Let’s look at that in detail:

UK-Based CSOC
We ensure the highest standards of security measures with on-shore UK-based cyber security experts on-demand.
Sentinel SIEM
We manage and review automated incident response using the advanced and cloud-native Azure Sentinel security information and event manager.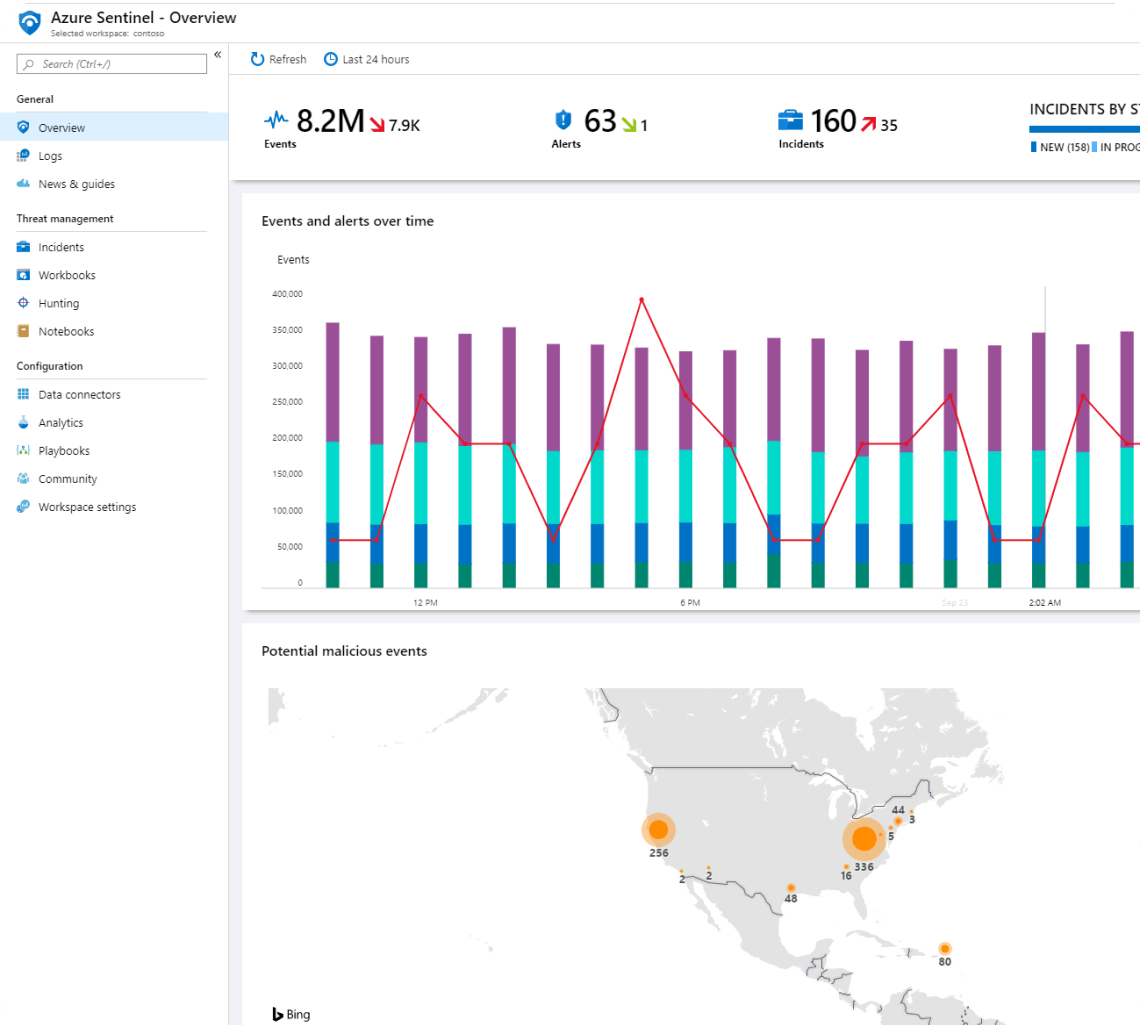
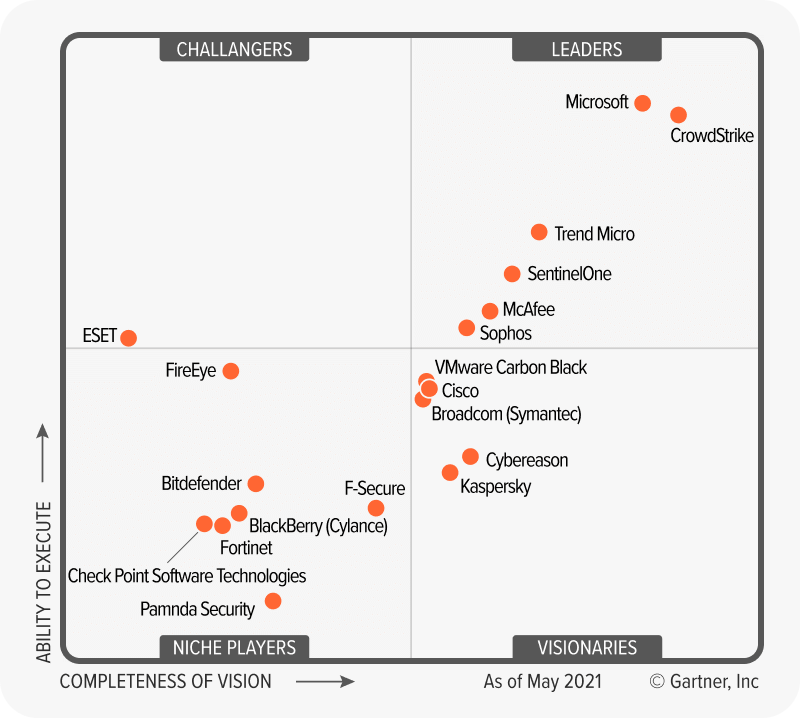
Microsoft Defender for Endpoint
We deploy technology identified by Gartner as the industry-leading endpoint solution to automate our response capabilities and deploy human expertise to best effect.
Threat Intelligence
We issue regular updates to ensure that you’re kept informed on the latest risks and are best placed to make any in-house changes needed to maximise the capabilities of our MDR services.
Creating defence-in-depth
The volume, variety and sophistication of cyber security threats have increased. With a growing number of organisations turning to flexible working, there are increased individual vulnerabilities such as:

Social engineering: For example, malware delivered by phishing attacks are harder to control and mitigate with BYOD and remote access.


Malicious code: Providing access to a wider range of devices used for personal and work contexts increases the risk of both planned and accidental uploads of malicious code.


Unpatched/outdated software: Non-standardised devices and out-of-office access make it harder to keep everything up-to-date and in-line with best practices.
- Fortify your cyber security with multiple layers of defence.
- Strengthen your cyber security defences and respond automatically to threats.
- Execute threat hunting strategies to detect and isolate advanced threats proactively with active cyber defence.
MDR ensures that if your front-line defences are breached, there are multiple security measures to prevent escalation. Fundamentally, MDR security is about identifying and responding to threats before they become a breach, and minimising the impact of any breach that occurs on your system as a whole.
How Six Degrees MDR Solves
Cyber Security Challenges
Check out our data sheet to learn about flexible and
cost-effective cyber security outcomes.
The technical foundation of MDR: endpoint security
MDR doesn’t exist without endpoint security, and it’s important to understand endpoint if you want to understand how MDR works and why it’s so important.

What is endpoint security?
Endpoint security focuses on monitoring and protecting the devices used on your network in order to prevent your system as a whole from being exposed by a breach of any specific endpoint.
Designed to detect, locate, analyse, and respond to cyber-attacks quickly, endpoint security is a flexible framework that still protects what’s important — keeping workstations, servers and infrastructure secure.
Although it can be deployed in isolation, it’s only truly effective with the 24×7 support of dedicated management and response resources.
MDR vs in-house monitoring
MDR capabilities can be delivered by an in-house monitoring and response team. But, for most organisations, the efficacy of the outcome isn’t the same.
To be effective, monitoring needs to be 24×7. On average, running a CSOC involves:
Managing 10,000 daily alerts
Allotting 20 minutes to triage one alert
Curating an integrated toolset able to reduce the number of tools required to get the job done.
A centralised and consolidated approach to cyber security response management provides more effective threat resolution at lower cost. Managed detection and response services are a critical part of doing more with less. Here’s why:


Economies of scale:
Operating on a large scale delivers cost savings. Partnering with a strategic MDR provider delivers more efficient access to the expertise and technology you need to match advanced threats in real-time without having to duplicate costly infrastructure in-house.


Sidestep the cyber skills shortage:
More than a quarter of UK businesses have an incident response skills gap — on top of the already strained cyber security job market. Overcome this challenge with MDR and gain direct (and on-demand) access to the vetted cyber professionals you need today.


On-demand expertise:
It’s more resource-intensive to respond to a threat than monitor activity. An MDR partner guarantees access to expertise without having to invest in full-time staff (including specialists) who aren’t always needed — helping you keep your costs and operation to a minimum.
Industry-leading MDR services from Six Degrees
MDR requires relying on a strategic partner to keep your organisation safe. You need to take that choice seriously. At Six Degrees, our MDR services combine best-in-class technology with industry-leading expertise and a cyber security philosophy that stresses automation, flexibility and defence-in-depth within the context of an ROI-centred focus on outcomes. Here are three components you need to consider:



Your cyber security journey: The threat landscape never stands still — neither can your response. Our cyber security strategy seeks to align your risk exposure with your risk appetite, and constantly updates best practices to minimise internal and external threats to deliver an efficient and effective outcome that matches your security posture.


The importance of Microsoft Defender for Endpoint: Our MDR solution is powered by Microsoft’s leading-edge endpoint security technology, and combines Microsoft Security Centre with Azure Sentinel and our Six Degrees CSOC for a multi-layered approach to cover endpoints, networks and cloud services. For businesses embedded within the Microsoft ecosystem, this delivers unbeatable comprehensive support within a holistic and effective solution. It also delivers the automation needed to respond in real-time and prevent threats from becoming a breach.


Doing more with less: We believe that cyber security should drive opportunities, rather than hold you back. By selecting flexible, cost-efficient and modern solutions, better outcomes can be achieved at a lower cost — enabling your organisation to demonstrate the true ROI of security, and stay ahead of risks.
Any incident response team requires the ability to monitor a system, deploy automated responses in real-time to manage and delay a breach, and then deploy human expertise to remediate the threat. At Six Degrees, we deliver this outcome using a unique combination of people, processes and technology — and you can access that expertise within a cost-efficient and sophisticated framework. Every organisation and industry is unique. Our bespoke deployment, configuration and management ensure that our solution is tailored to you.
A future-focused cyber security solution
Flexible and responsive cyber security capabilities are needed now more than ever, particularly in the context of remote working. We provide access to a best-in-class solution, delivering economies of scale while allowing you to sidestep the cyber security skills shortage.
Our cyber security teams supply the professional capabilities and cyber threat intelligence you need to focus on your core business, safe in the knowledge that your systems are secure and ahead of cybercrime trends. Being part of MISA demonstrates that we have the knowledge and context needed to get the most out of your Microsoft system, and our broader accreditations including GIAC, CHECK, Crest and CISSP enable us to connect that with your entire technology base.
At Six Degrees, we will:
- Review your existing infrastructure and provide an expert solution configuration.
- Strengthen your cyber security defences and respond automatically to threats.
- Use technology to automate the blocking and containment of threats.
- Deploy human expertise to manual triage incident prioritisation and alert analysis from a UK-based CSOC.
- Deliver threat analytics and investigation enabled by on-demand access to expertise.
- Guarantee security monitoring in real-time 24×7.
The reputation and business cost of security breaches is so much higher than their prevention. MDR is the best way to address cyber security now and in the future. MDR from Six Degrees will deliver defence in depth, enabling you to do more with less and guiding you safely on your cyber journey.
Deploy next-level MDR protection from Six Degrees today!
Access robust, automated and flexible cyber security outcomes able to match the demands of the modern and hybrid workplace. Get in touch to start protecting your system today.
We have serious credentials when it comes to delivering cyber security services.










Additional Resources
This report will provide a snapshot of key trends impacting cyber security and the risk landscape. We will then use those insights to identify sustainable and long-term answers to pressing cyber security questions.


Protecting your organisation’s network is all about taking calculated risks and reducing threats. But how can you ensure that you’re making space for uncertainty in your strategy, as well as communicating its importance to the board?


How will you respond to the growing sophistication of cyber security threats?
– Can you evolve your infrastructure to remediate threats continually?
– Are you in a position to use technology to automate the blocking and containment of threats?


